Getting Google reviews for your business has never been more important. Consumers are scouring the internet for online reviews to help them in their purchase decisions, and Google’s new search algorithm is designed to lead people to high-quality products and services. How Google changed search results Google now automatically aggregates and includes online reviews to displa... read more
Blog
Click on an article below to read more
Storms, floods, fire, and other emergencies can cause productivity loss due to power failure. Utilizing an uninterruptible power supply (UPS) for your workstations will ensure that you never lose unsaved work. But what about your online connection? To avoid being crippled by loss of internet connection, it’s a good idea to plug routers, wireless access points, and cable modems... read more
Back in the day, simple antivirus software was all you needed to stay safe from security threats. Nowadays, it takes more than that to protect your online privacy. Whether you’re sending emails or chatting up a friend online, chances are your Wi-Fi connection can be intercepted. This is why you need a virtual private network (VPN). Here’s how to choose one wisely. What is a ... read more
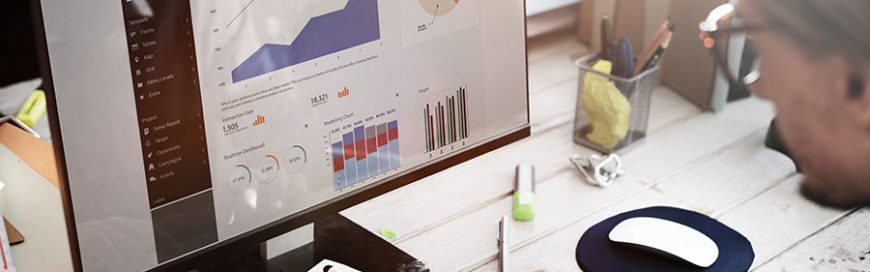
Measuring productivity is an important process in an employee’s performance evaluation. Previously, Microsoft’s Office 365 had MyAnalytics, a tool for employees to monitor their own performance. But Microsoft improved on it with Workplace Analytics, which now allows managers to also view and evaluate their staff’s productivity. Managers can use this data to create strat... read more
Businesses are always looking for ways to save a bundle without sacrificing growth. For a while, they believed that they had to buy workstations with their own processing power, RAM, and hard drive. But thanks to virtualization, companies can increase their revenue and get the computing processes they need with thin and zero clients. What are thin and zero clients? Thin clients ... read more
When you spend more than eight hours a day staring at a computer screen, it can be easy to lose focus on important tasks. While you can access some of the most useful applications through your computer, an ever-growing number of distractions are vying for your attention. Here are a few tricks to avoid getting distracted at work and boost your productivity. Monitor productivity l... read more
Google Chrome is the most popular web browser in the world with over 2 billion installs, 1 billion users, and 53% share of the market. Its speed is one of its most notable advantages over other existing browsers, as well as one of the reasons why it’s preferred by most netizens. But even the fastest browser experiences some performance drops from time to time. If your Chrome h... read more
Office 365 just keeps getting better and better. Check out how these new and upcoming enhancements can improve productivity. Office Write and draw with digital ink Typing is easy on desktops and laptops, but when you’re on touch-enabled devices, keyboards are cumbersome to use, whether they are extra hardware or as space invaders on your screen. Now, the Draw tab is available ... read more
For years, we’ve been told that strong passwords include three things: upper- and lowercase letters, numbers, and symbols. And why wouldn’t we when the National Institute of Standards and Technology (NIST) told us they were the minimum for robust passwords? Here’s why not and how it involves you. The problem The issue isn’t necessarily that the NIST advised people to cre... read more
While mobile devices cannot equal what desktops and laptops can do, they’re inching pretty close to matching them. That’s why businesses are allowing their employees to use their smartphones and tablets, which help increase productivity and enhance collaboration. But mobile devices have also become the new targets of cybercriminals. Protect your devices with the following ti... read more
As technology grows, more solutions are available to help businesses cut costs and improve efficiency. One such solution is software as a service, aka SaaS. To know if this can benefit your business, it’s best to learn what SaaS actually is. Read on for the answers. What is SaaS and what makes it appealing? SaaS is a software delivery model that allows the user to access softw... read more
No business owner should ever be embarrassed by their website. It’s worth the effort to run through everything with a fine-toothed comb and ensure your online customers are getting the best possible experience. We’ve rounded up the top six website elements you need to invest in. A variety of professional photos From pictures of your products to team photos, high-quality imag... read more
Your company may be done migrating to Office 365, but there’s still a lot you must do. Now that your productivity tools are online via the cloud, there are a few optimizations that will provide your users with a better experience. Declutter your inbox If you’re having trouble managing the overwhelming amount of emails in your inbox, then using Office 365’s “Clutter” fe... read more
What do you call someone who hunts for security gaps in computer hardware and software? A hacker, right? What about someone who presents their findings to vendors to help them improve the quality of their products? There is more than one type of hacker, and understanding the difference is important. A complicated history In the 1950s, the term 'hacker' was vaguely defined. As co... read more
Your Internet of Things (IoT) devices — smart TVs, security cameras, smart locks — add a level of convenience to your workplace, but they also make your systems more vulnerable to cyberattacks. That’s because they’re essentially potential entry points for hackers. Here are some ways to secure your IoT devices from a possible cyberattack. Set passwords Not many people kno... read more
Time is of the essence, especially for small- or medium-sized businesses. To keep up with your competitors, spending most of your day rummaging through your inbox won’t help. Use these Gmail tips and tricks and spend less time in front of the monitor and more time enhancing your bottom line. Undo Send We’ve all had an email or two we wish we could take back. Gmail has a neat... read more
Smartphones have become so advanced that there's virtually no business task they can't handle. Now everyone uses mobile devices to access work documents and, naturally, hackers got the memo. There are thousands of threats targeted towards mobile devices, so you’d be well served backing up the files in your mobile device, now. Malware on mobile More than two-thirds of the world... read more
For businesses, data security is critical. If this information is lost or stolen, it could lead to crippling financial losses, legal disputes, and more importantly, loss of customer trust. While Microsoft Office 365 comes with some security and compliance tools, it still needs the support of data protection best practices. Here are seven you should consider. Take advantage of po... read more
While many IT providers tout the revolutionary benefits of the cloud, very few address the security aspect of it. The fact is, when you’re using a cloud service, you’re moving information out of your hands and into a third party. So doesn’t it make sense to take precautions? Dropbox alone has had the accounts of nearly seven million users hacked. That being said, it’s wi... read more
Social media marketing can be tricky simply because there are so many platforms to choose from. Your first instinct might be to choose Facebook because it is the biggest name in the industry and has the widest reach, but just because it’s effective for other businesses doesn’t mean it will also match your business goals. Every business is different, so decision makers should... read more
Are you still using that old computer that is not-so gracefully aging and devaluing? Maybe you are running important programs on older machines with old operating systems since they “still work fine.” While it might still help you get the job done, there may be hidden security risks that can lead to major problems later on. What is firmware? Firmware is a basic type of softw... read more
Any successful small- or medium-sized business today must do two things to thrive: digital marketing and network security to keep its data safe from cyber attacks and other forms of data loss. When it comes to security, browsers are no exception. In small- and medium-sized businesses, some 50 to 150 workers access the net daily through the company network via browsers on your de... read more
Businesses need technology to be profitable and productive. But not all technologies are capable of delivering on their perceived benefits. To make sure your investments are still worth keeping, you need to perform technology business reviews. What is a technology business review? A technology business review reveals the strengths and weaknesses of your company’s IT framework.... read more
Microsoft not only builds robust productivity solutions for its customers, but it also prioritizes their security above all else. This year, the company invested a lot of money to protect Office 365 subscribers from increasingly sophisticated phishing scams. Read on to learn more about what they did. Effective anti-phishing solutions must be able to recognize the key elements of... read more
Most managed IT services providers (MSPs) promise “proactive” cybersecurity consulting. Businesses large and small embrace the idea of preventing cyberattacks and data breaches before they happen, and MSPs themselves would much rather brainstorm safeguards than troubleshoot time-sensitive downtime events. But it’s not always clear what proactive cybersecurity means, so let... read more